Is SCADA secure against cyber security threats?
Cyber security has become an increasingly important issue, with the control systems of critical infrastructure becoming a potential target of hackers. In the past, control systems were isolated from other networks, however modern systems are complex, digital and connected, with data required to be transferred between industrial and external networks. This creates a potential for malware and hackers to access and disrupt the system. While these threats are real, there are steps that can be taken to ensure control systems are more secure.
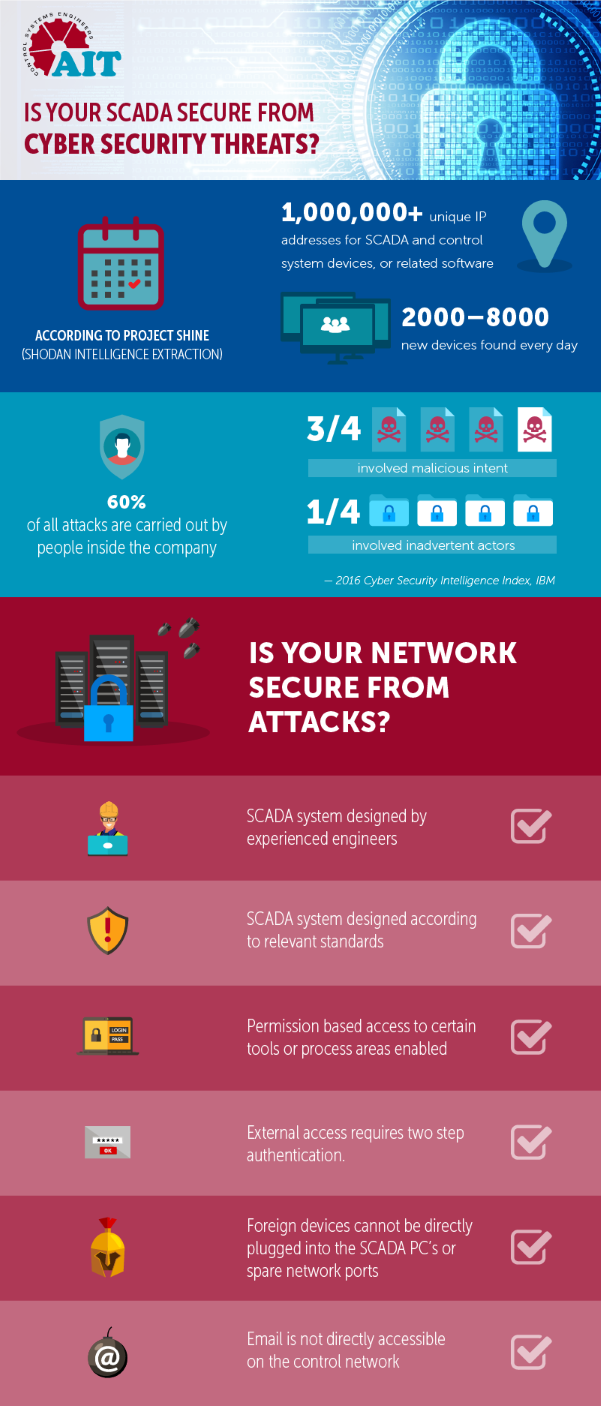
One million connections and counting
According to data from Project SHINE (SHodan Intelligence Extraction) - which was developed to extract information about existing SCADA and industrial control systems (ICS) from the internet using an online search engine called SHODAN - by January 2014 there were over one million unique IP address that belonged to either SCADA and control system devices, or related software. At the time, the project on average was finding between 2000 and 8000 new devices every day.
The internet is public domain, and everything attached to it can be seen and accessed by anyone, anywhere, anytime. If SHODAN, Google or Yahoo can gain access to a SCADA, control system device or software product, then so can the hackers.
While cyber attacks on SCADA systems have, so far, been rare, the number of attacks have been rapidly increasing in proportion to the number of control systems devices.
A Trend Micro experiment showed the potential for cyber attacks on control systems by creating a honeypot net - a decoy to lure cyber attackers - on the internet, which mimicked 12 municipal water control systems in various countries and simulated a real-time system to attract attackers.
Over the course of three months, several targeted attacks were recorded, with a number of these able to compromise the entire operation of the control system device. Attacks came from 16 countries, accounting for a total of 74 attacks on seven of the honeypots. 10 of these were considered critical.
As these attacks occurred on a honeypot there was no wider impact, however failure or security breaches of a real system could result in wide-reaching impacts, not only for the organisation, but for the community and economy, depending on the criticality of their goods or services.
For example, impacts on critical infrastructure could include wide-scale blackouts due to electricity grid failure, an oil or sewage pipeline releasing its contents, or loss of control of the system causing extensive disruption.
Securing control networks
Working at a systems integration company, Geoff Bladon, Business Development Director at Automation IT, said engineers come across vulnerable control systems on a monthly basis, however there is a growing focus towards security of control systems.
“Most SCADA software allows permission based access to certain tools or process areas, however a lot of end users don’t take advantage of this. One of the biggest issues we see is SCADA systems that are very loosely secured by allowing administrative rights to operators or having passwords on post it notes stuck on the side of the PC,” Mr Bladon said.
“However, cyber security is becoming an increasing consideration for control systems. It’s great to see people thinking about cyber security when they design a system, however there is still a long way to go and lots of end users think they are safe when they most certainly are not.”
It is imperative that control systems are designed by experienced engineers who are up-to-date with the latest in automation and cyber security technology, trends and standards, to minimise the chance of a cyber attack.
“When designing a control network we are responsible for ensuring it is designed is such a way as to minimise the probability of cyber attack from external parties and by unintentional misuse from within,” Mr Bladon said.
“We use a range of industry proven methods and regularly attend industry briefings from global manufacturers and cyber security experts. We currently have engineers studying to obtain tertiary qualifications in cyber security while also working full time, we are dedicated to keeping our customers protected.”
Mr Bladon said it’s important to look closely at the interconnection of the control network, connection to corporate networks and the internet when designing a control system.
“Ensuring external access is authenticated and not direct, ensuring foreign devices such as USB keys cannot be directly plugged into the SCADA PC’s, ensuring foreign laptops cannot be plugged into spare network ports, and lastly ensuring email is not directly accessible on the control network are some of the main problems we look for when installing a system as these are all areas which could compromise its security.”
Standards also play an important role in ensuring a control system is as secure as possible.
“The ISA99 and IEC62443 standards are a great resource, and cover most of the commonly encountered issues and how to avoid them. If all plants based their systems on the principles outlined in IEC62443 it would make the hackers job a lot harder,” Mr Bladon said.
“There are number of simple things people can do like disabling spare ports on network switches, disabling email and not providing spare USB connectivity on SCADA computers, for example, to try to minimise the payload from making it’s way physically onto the network.”
Maintaining security after installation
While having a securely installed control system is a major factor in minimising security breaches, asset owners also need to be aware of the everyday activities and employees that can compromise the security of the system.
An IBM report, 2016 Cyber Security Intelligence Index, found that 60 per cent of all attacks were carried out by people inside the company, with three-quarters of attacks involving malicious intent and one-quarter involving inadvertent actors.
Knowing who can gain access to the control system and how they are able to do it is a key consideration for asset owners. It is also important to remember people make mistakes, so ensuring staff know how to properly use the system and are educated about what can compromise it, will help to prevent inadvertent compromisation of the system,” Mr Bladon said.
“Security of control systems is a problem that asset owners need to be aware of, and actively making decisions about how to best protect their systems. By choosing an experienced systems integrator that is up to date with the latest standards and trends, as well as being aware of how employee activities can affect the system, asset owners can be assured their systems will be extremely well protected from security compromises, both internal and external.”

